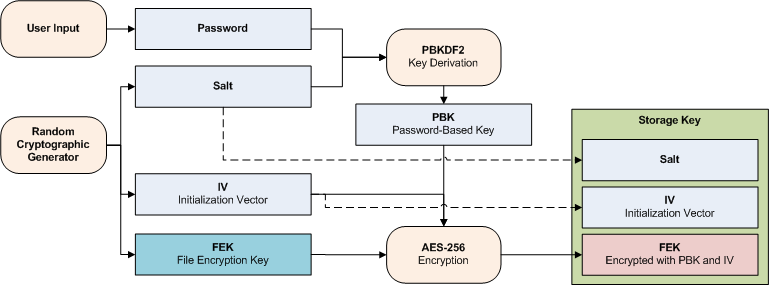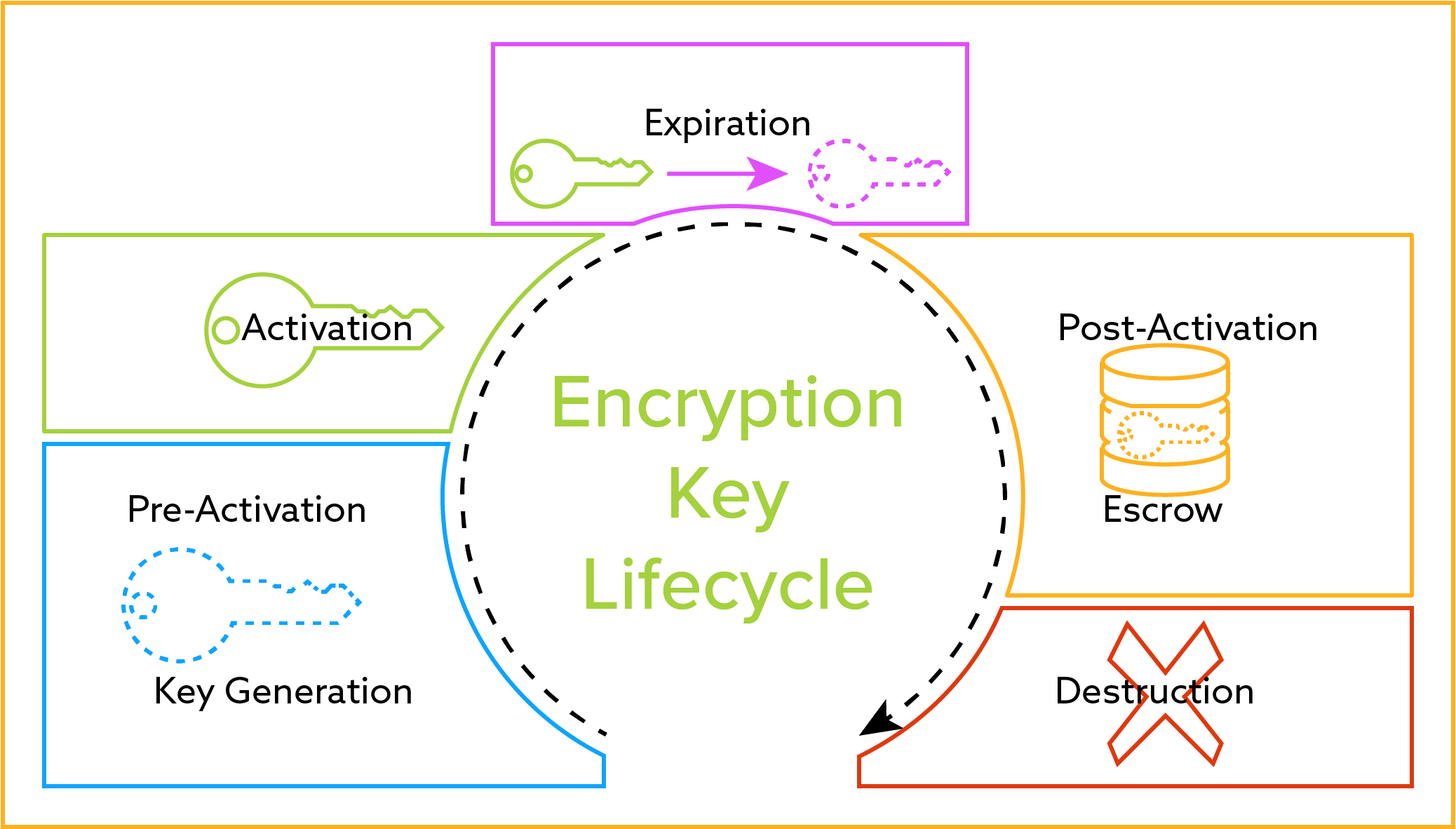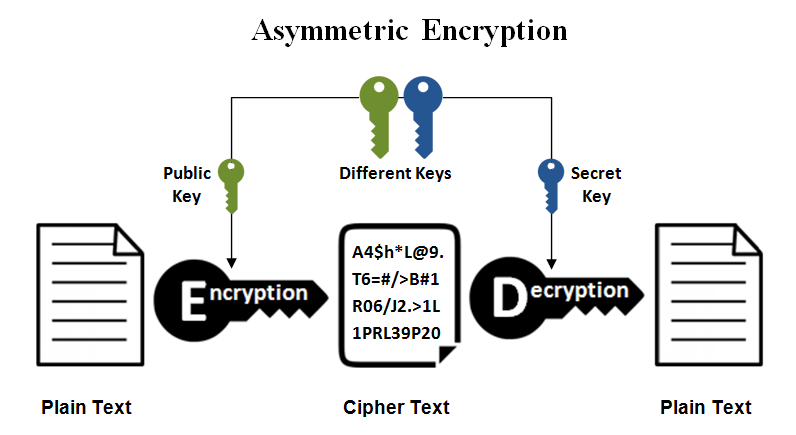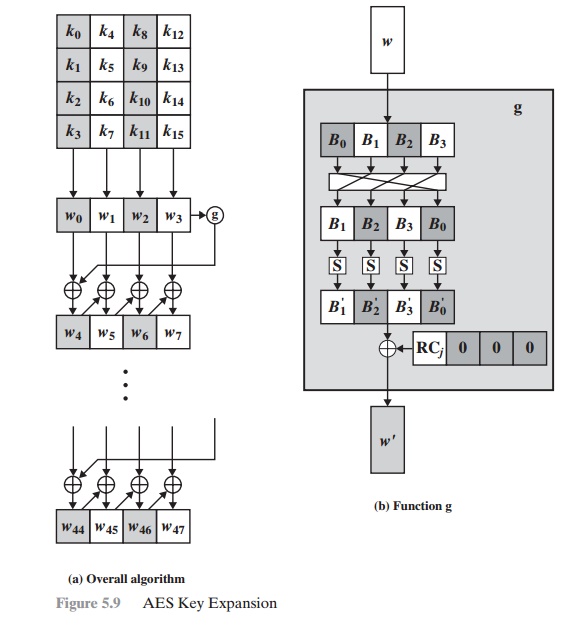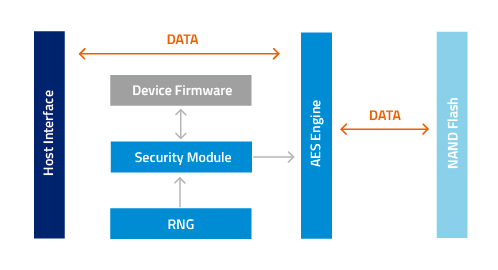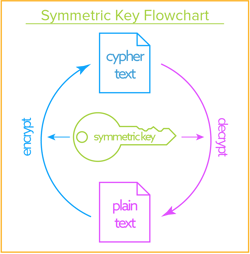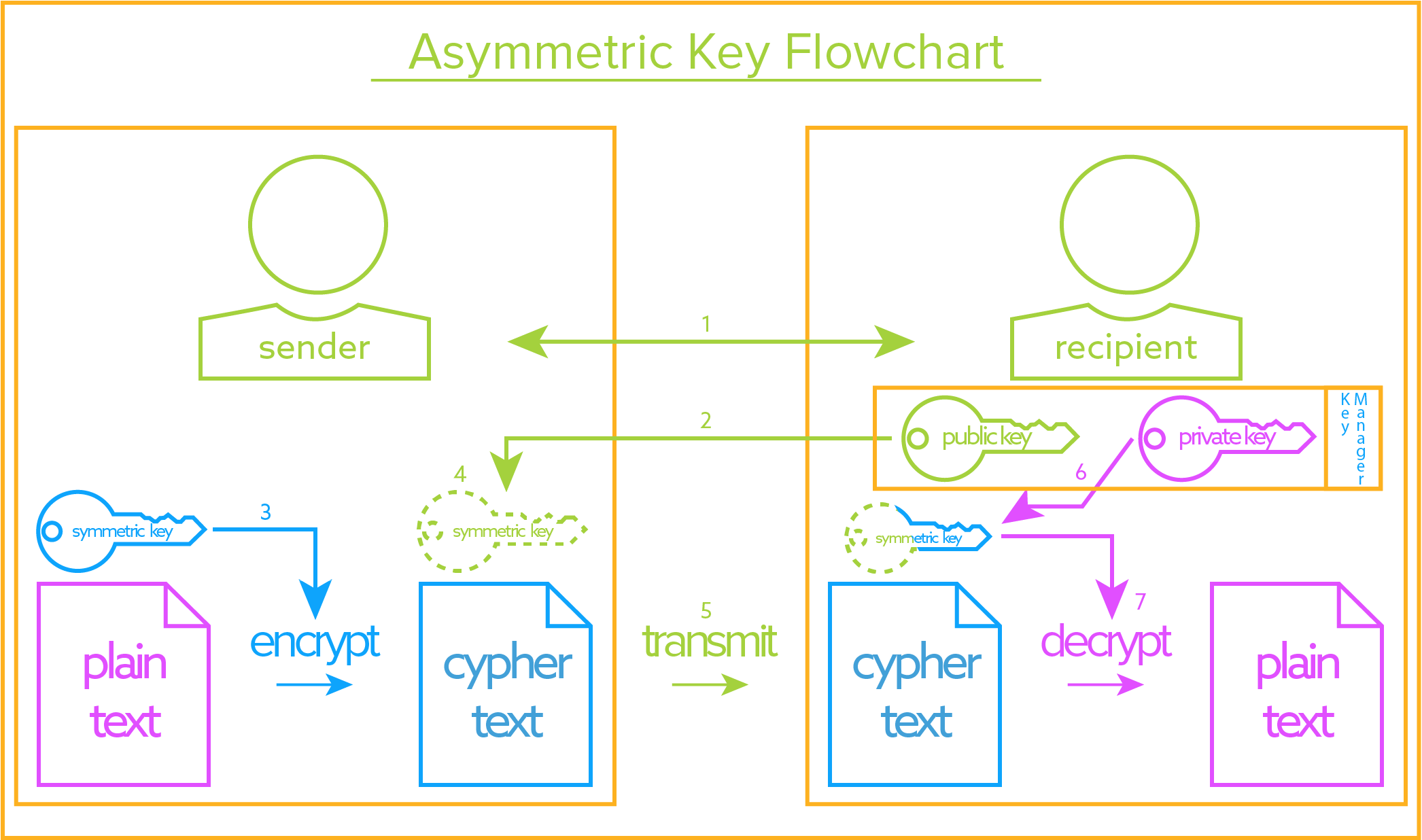
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm

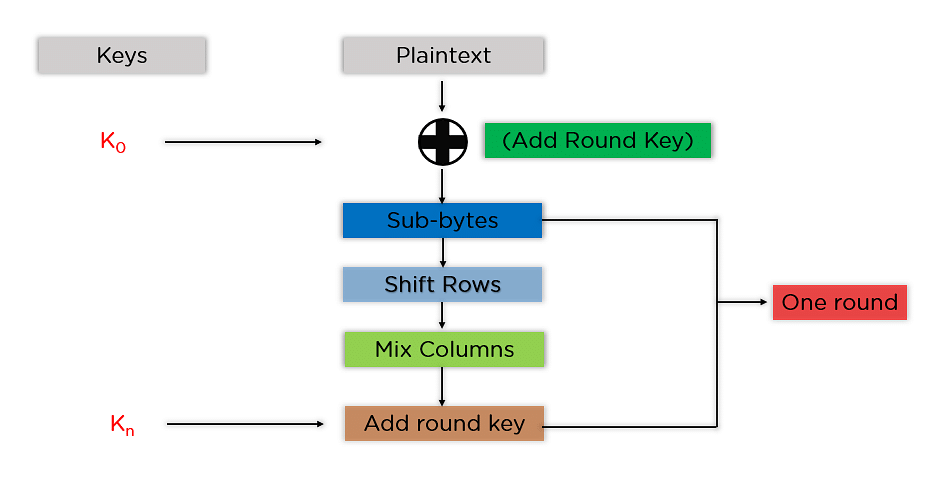
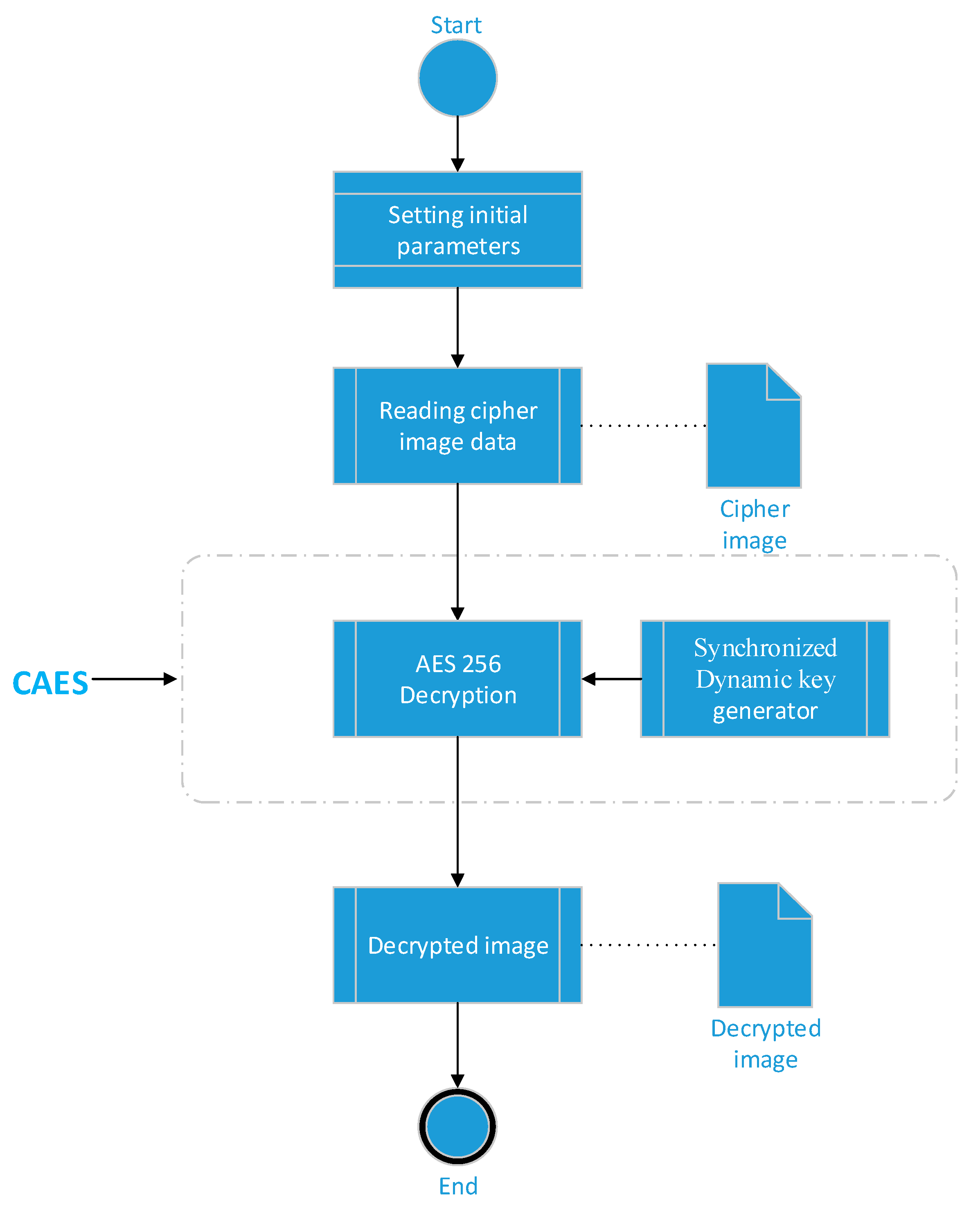
A flow chart of the generic AES-256 algorithm steps for encryption and... | Download Scientific Diagram